Zero Trust Security Approach and its Benefits
Today’s industrial environments often have complex networks with a wide range of interconnected systems and devices, which can make them more vulnerable to cyberattacks and other security threats. Industrial networks typically are highly heterogeneous, with a variety of different technologies, protocols, and vendor tools in use. Furthermore, devices and users often connect and disconnect frequently from the network which makes the system difficult to monitor and control.
A few challenges an industrial organization faces in ensuring security are Complex and evolving threats, Limited visibility and control, Lack of standardization, Constraints on network performance, & Limited resources
Zero Trust Security is a security approach that is based on the idea that organizations should not automatically trust anything inside or outside of their network perimeter. Instead, organizations should verify the identity of every user and device before granting access to the network, and then continuously monitor network activity to ensure that only authorized users and devices are allowed to access sensitive resources.
Guiding Principles of Zero Trust Security
Never trust, always verify
This is the core principle of zero trust security, which means that all network traffic must be treated as untrusted and must be verified before access is granted.
Verify the user and device
Zero trust security requires that users and devices be authenticated and authorized before they are allowed to access network resources.
Verify the network and data
In addition to verifying the user and device, zero trust security also requires that the network and data be verified to ensure that they are safe and secure.
Continuously monitor and respond
Zero trust security requires constant monitoring of the network and its traffic, and the ability to quickly respond to any potential threats or security incidents.
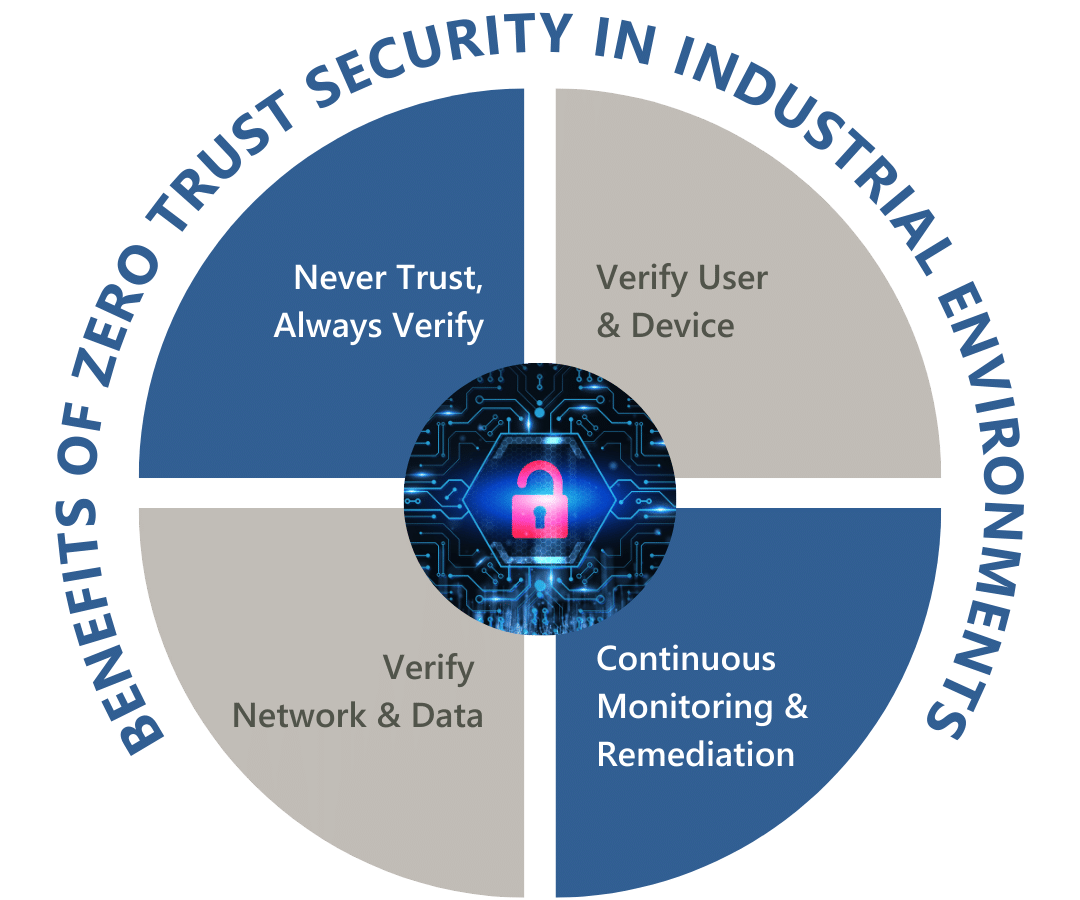
Benefits of Zero Trust Security in Industrial environments
Better visibility and control
Zero trust security can provide industrial organizations with greater visibility and control over their networks and network traffic, allowing them to identify and respond to potential threats more quickly and effectively
Reduced Downtime
Industrial networks are often critical to the operation of manufacturing, energy, and other industrial processes. Zero trust security can help to prevent downtime caused by security incidents, which can have significant financial and operational impacts.
Improved security
Zero trust security can help to prevent unauthorized access to industrial control systems and other sensitive equipment, reducing the risk of cyberattacks and other security incidents.
Enhanced compliance
Industrial organizations are subject to various regulations and standards that require strong security measures, such as the North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) standards. Zero trust security can help industrial organizations to comply with these requirements
Written By

Would like to know more?
Contact our experts to know the best cyber security model that works for your industry.
