Network Access Control (NAC) with The Zero Trust Model
Today, when assets are constantly connecting and disconnecting from the network, the security risks they bring along with, is potentially high. Employees, clients, vendors etc. will all have different needs from corporate data of an organization and the levels of access to information will be different for all.
Managing the “n” number of resources, connections and user access could pose complex in such a scenario. When cloud-based architectures are involved, single, multiple or hybrids, the resources are likely to be scattered across numerous IT ecosystems. Ensuring that the right users have access to the right amount of right information under secured conditions can be challenging and this forms the underlying motive of the Zero Trust Security Model.
Never Trust, Always Verify is the fundamental rule followed by the Zero Trust Security approach wherein no matter who the user is, or device be, if they are a previously verified user or connected to a permissioned network, they must always be authenticated, authorized, and validated before being granted access to the resources required per tasks at the micro segmented network layers.
Guiding Principles of Zero Trust Security
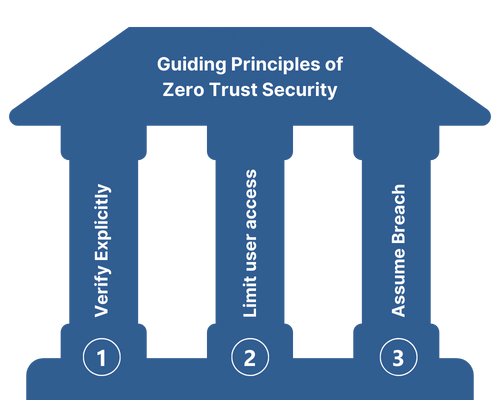
Verify Explicitly
Authenticate and authorize only after a thorough verification of user and endpoints.
Limit User Access
Limit user access to provide just enough access for just enough time
Assume Breach
Assume Breach is a paradigm to treat that a breach has already occurred, and accounts have been compromised.
Features of Network Access Control with Zero Trust Network Access (ZTNA)
Today, there has been an exponential shift from desk-based jobs to a work culture that suit individuals to work from anywhere. With employees working remotely and the demand for IoT solutions rising at a peak, a new era of Cyber Security arises wherein security officers must be capable of managing Enterprise of Things and BYOD (bring your own devices) effectively. For this, the requisite of a secure network access control has not been more critical. To combat this, the implementation of secure NAC is administered with Zero Trust Security.
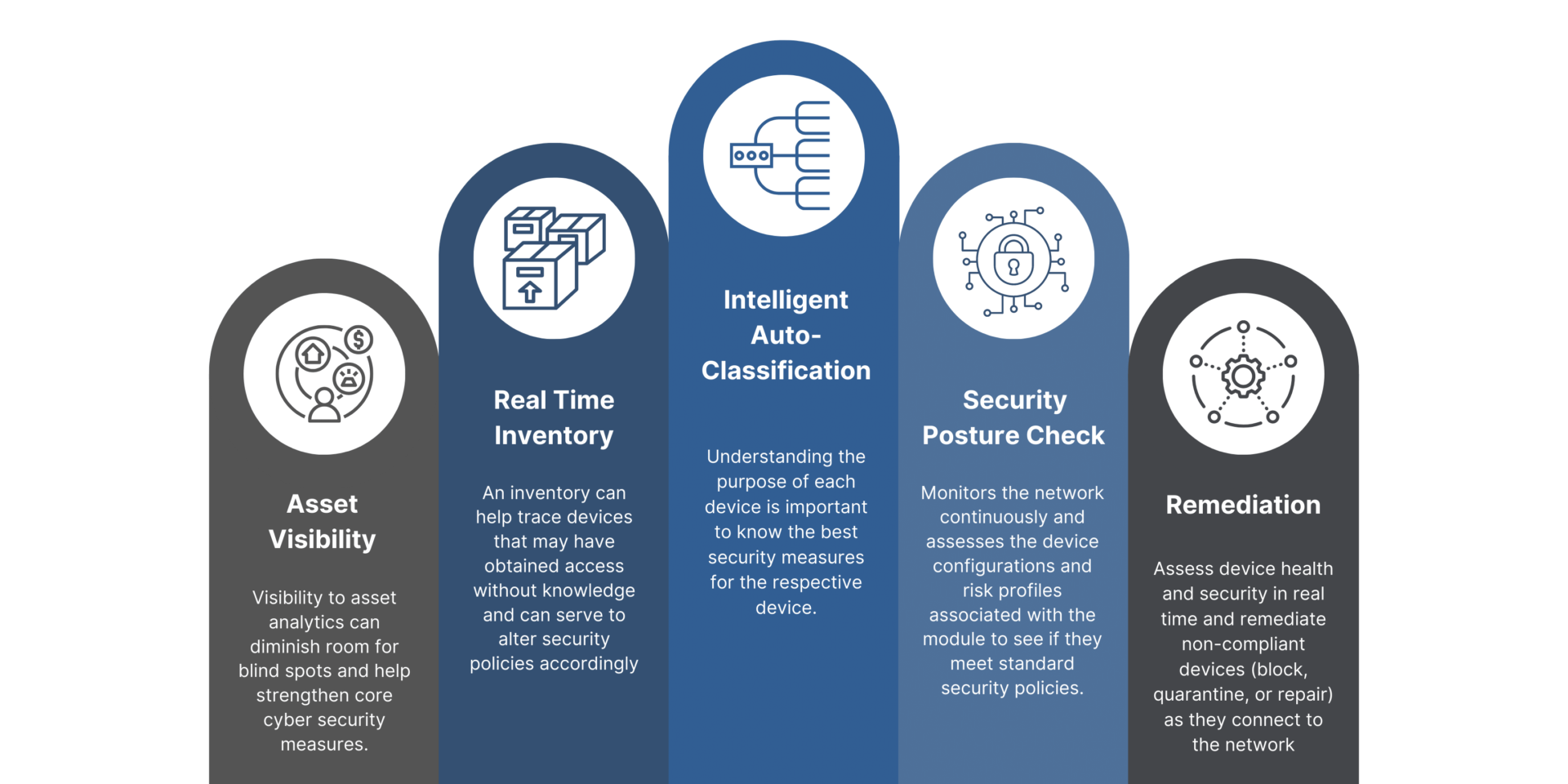
Asset Visibility
Visibility to asset analytics can diminish room for blind spots and help strengthen core cyber security measures. A well-defined platform should be able to provide a holistic view of devices across the enterprise network along with necessary measures to control all managed and unmanaged users / devices as they join the network.
Real Time Inventory
A real time directory to keep track of device configurations, compliance stats with access levels or unusual user activity. An inventory can help trace devices that may have obtained access without knowledge and can serve to alter security policies accordingly.
Intelligent Auto-Classification
The profiler is a module that automatically collects data about endpoints (such as device type, operating system, vendor, and model) by analyzing data packets sent by these systems in the networks. Understanding the purpose of each device is important to know the best security measures for the respective device. This can be used for policy creation and automated onboarding processes for larger groups of similar endpoints.
Security Posture Check
On understanding the operational purpose of the device, an additional requirement of evaluating if the module is in its best health or not, also prevails. The security posture check monitors the network continuously and assesses the device configurations and risk profiles associated with the module to see if they meet standard security policies.
Remediation
If devices pose a risk, security policies immediately take over to mitigate threats without the need of an administrator to attend.
Would like to know more?
Contact our experts to know the best cyber security model that works for your industry.
