ICS Cyber Security in UAE's Oil & Gas Industry
The UAE, in recent years has set foot to becoming a leader in Digital Innovation and Technologies, competing among nations to adopt digitalization technologies across all sectors. The increased digitalization initiatives have also raised demand for OT cyber security solutions.
The Oil & Gas sector in the Middle East stand susceptible of being prime targets to cyber-attacks and if not dealt with caution, damage could be massive. After the multiple Shanoon virus attack on the Oil and Gas Giant, Saudi Aramco, in 2011 and further in 2016 and 2017, the governments have instigated every Oil and Gas company to develop stronger cyber defense strategies.
As indicated in 3 Step Approach to exacting Cyber Security in Oil & Gas Industry, we see that the exponential rise of cyber-attacks in the Oil and Gas, have taken place through the passive OT systems upon convergence of the OT and IT technologies. The coining of the two technologies form core of any Industry 4.0 Digital Transformation strategy and persists as an unquestionable must have.
Are the Oil and Gas industries in UAE Cyber secure?
And if so, are they clever and robust enough to uphold incoming threats?
If you are part of Oil and Gas industry and working on OT Cyber Security related initiatives, CONSYST may be able to help you out.
CONSYST Middle East is a leading Industry 4.0 Automation and Digitalization solutions provider, crafting robust OT-IT integration and IIoT Solutions.
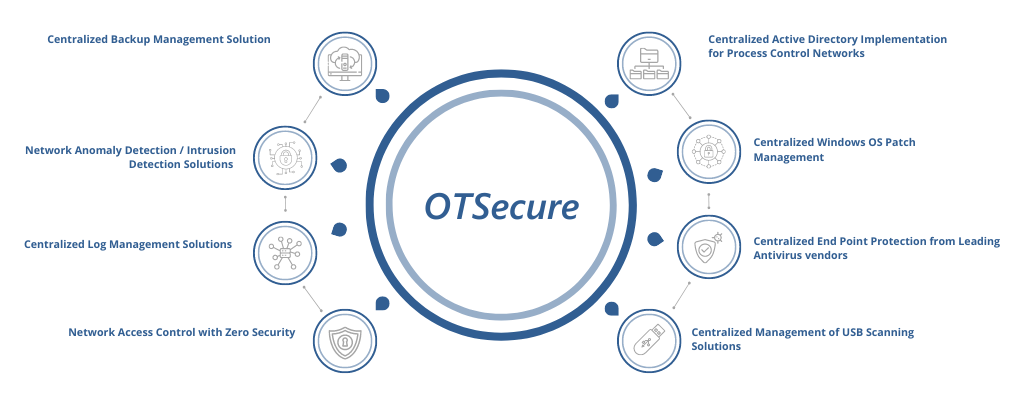
Cybersecurity across OT, SCADA and ICS are all areas of concern when it comes to Oil and Gas Industry. OTSecure®, our packaged cybersecurity-solution-in-a-box helps provide a fundamentally robust, seamless, and holistic cyber security solution to secure such critical infrastructure as below.
Creating an organization structure and mapping the users and devices to the structure to provide the right amount of authentication and access to the network along with timely clean up and maintenance
Process of enabling patches for Windows, from scanning to, detecting, downloading, and deploying automatic patch management solutions
To manage endpoint security centrally to protect, detect and address impact across the network from any location at any time. Administrators can order updates and patches across the devices automatically without having to rely on individuals to carry out updates on their machines
USB Device Control enable administrators to centrally scan USB devices connecting to the network. Administrators can authorize access, block, or disable them enabling unauthorized download / upload activities into the network
A data management strategy to help create and manage backups of all tasks from all backend devices from a single central computer managed by a single administrator
Continuous monitoring of the network to find and fix incidents before they become an incident
Centralized logging solution to collect logs from multiple servers and consolidate data. The data collected will be at a centralized repository to ease access, streamline and automate manual log management
To ensure that all users and devices connecting to the network are first verified and then trusted to a limited access